New disclosures from Edward Snowden show the NSA is massively expanding its computer hacking worldwide. Software that automatically hacks into computers – known as malware “implants” – had previously been kept to just a few hundred targets. But the news website The Intercept reports that the NSA is spreading the software to millions of computers under an automated system codenamed “Turbine.” The Intercept has also revealed the NSA has masqueraded as a fake Facebook server to infect a target’s computer and exfiltrate files from a hard drive. We are joined by The Intercept reporter Ryan Gallagher.
How the NSA Plans to Infect ‘Millions’ of Computers with Malware
By Ryan Gallagher and Glenn Greenwald, The Intercept
Top-secret documents reveal that the National Security Agency is dramatically expanding its ability to covertly hack into computers on a mass scale by using automated systems that reduce the level of human oversight in the process.
The classified files – provided previously by NSA whistleblower Edward Snowden – contain new details about groundbreaking surveillance technology the agency has developed to infect potentially millions of computers worldwide with malware “implants.” The clandestine initiative enables the NSA to break into targeted computers and to siphon out data from foreign Internet and phone networks.
The covert infrastructure that supports the hacking efforts operates from the agency’s headquarters in Fort Meade, Maryland, and from eavesdropping bases in the United Kingdom and Japan. GCHQ, the British intelligence agency, appears to have played an integral role in helping to develop the implants tactic.
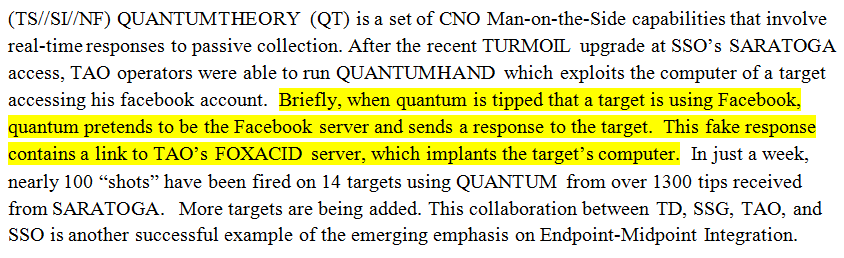
In some cases the NSA has masqueraded as a fake Facebook server, using the social media site as a launching pad to infect a target’s computer and exfiltrate files from a hard drive. In others, it has sent out spam emails laced with the malware, which can be tailored to covertly record audio from a computer’s microphone and take snapshots with its webcam. The hacking systems have also enabled the NSA to launch cyberattacks by corrupting and disrupting file downloads or denying access to websites.
Mark Zuckerberg calls Obama after NSA report
By Alex Byers, Politico
Facebook CEO Mark Zuckerberg called President Barack Obama Wednesday night to complain about U.S. government actions that are undermining trust in the Internet, after a report that described how the National Security Agency posed as a Facebook server to inject malicious software into targets’ computers.
“When our engineers work tirelessly to improve security, we imagine we’re protecting you against criminals, not our own government,” Zuckerberg wrote in a Facebook post Thursday. “The U.S. government should be the champion for the internet, not a threat. They need to be much more transparent about what they’re doing, or otherwise people will believe the worst.” [..]
Zuckerberg did not make direct reference to the report in The Intercept. But he said he expressed frustration to the president about the “damage the government is creating for all of our future.” He added, “Unfortunately, it seems like it will take a very long time for true full reform.”
The NSA has denied doing any of this which flies in the face facts revealed in it’s own secret documents. Ryan Gallagher discusses those documents
A particular short excerpt from one of the classified documents, however, has taken on new significance due to the NSA’s statement. The excerpt is worth drawing attention to here because of the clarity of the language it uses about the Facebook tactic and the light it shines on the NSA’s denial. Referencing the NSA’s Quantum malware initiative, the document, dated April 2011, explains how the NSA “pretends” to be Facebook servers to deploy its surveillance “implants” on target’s computers:
It is difficult to square the NSA secretly saying that it “pretends to be the Facebook server” while publicly claiming that it “does not use its technical capabilities to impersonate U.S. company websites.” Is the agency making a devious and unstated distinction in its denial between “websites” and “servers”? Was it deliberate that the agency used the present tense “does not” in its denial as opposed to the past tense “did not”? Has the Facebook QUANTUMHAND technique been shut down since our report? Either way, the language used in the NSA’s public statement seems highly misleading – which is why several tech writers have rightly treated it with skepticism.
The same is true of the NSA’s denial that it has not “infected millions of computers around the world with malware” as part of its hacking efforts. Our report never actually accused the NSA of having achieved that milestone. Again, we reported exactly what the NSA’s own documents say: that the NSA is working to “aggressively scale” its computer hacking missions and has built a system called TURBINE that it explicitly states will “allow the current implant network to scale to large size (millions of implants).”

Recent Comments